Network Security - Part 7: Remote Access & VPNs
In today’s world, It’s very common for companies to have multiple offices around the world and to allow employees to work remotely. This desired for mobility must be taken into consideration when designing your network to ensure people can access company resources from anywhere, at anytime, and with a high degree of security. The most common remote access technology used today are Virtual Private Networks (VPNs).
At a high level, a VPN allows users to access corporate assets (email servers, web applications, shared folders, etc…) remotely, just like they would if they were connected to the internal network. There are two main types of VPNs.
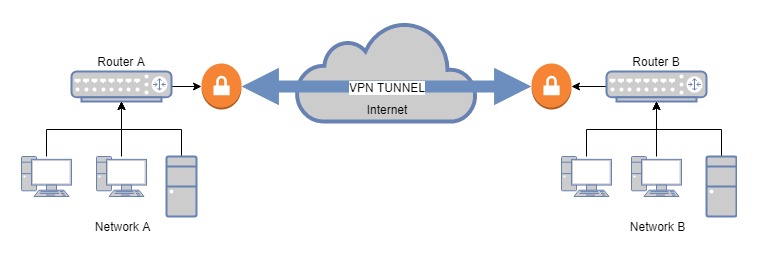
Site-to-Site or Point-to-Point VPNs connect two or more networks:
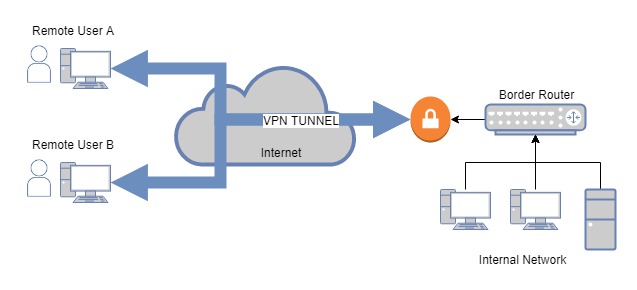
Whereas Remote Access VPNs allow users to connect to a site from a remote location (e.g. home office):
Though the concept is the same, the underlying technology varies greatly depending on which VPN type you want to implement. In this post, we will discuss how to configure our pfSense router to serve as a Remote Access VPN server using a popular software called OpenVPN.
Create Certificates
Two of the most important services that VPNs provide are confidentiality (making sure the communication is encrypted to protect data in transit against eavesdropping attacks) and authentication (ensure that remote users are who they claim to be before granting them access to the internal network).
Confidentiality is achieved through the use of encryption and digital certificates. Authentication can also involve certificates (i.e. certificate-based authentication) but that is not the only way. Most VPN servers support standard username and password credentials as well. Most of them even integrate with you standard corporate user repository such as Active Directory or LDAP.
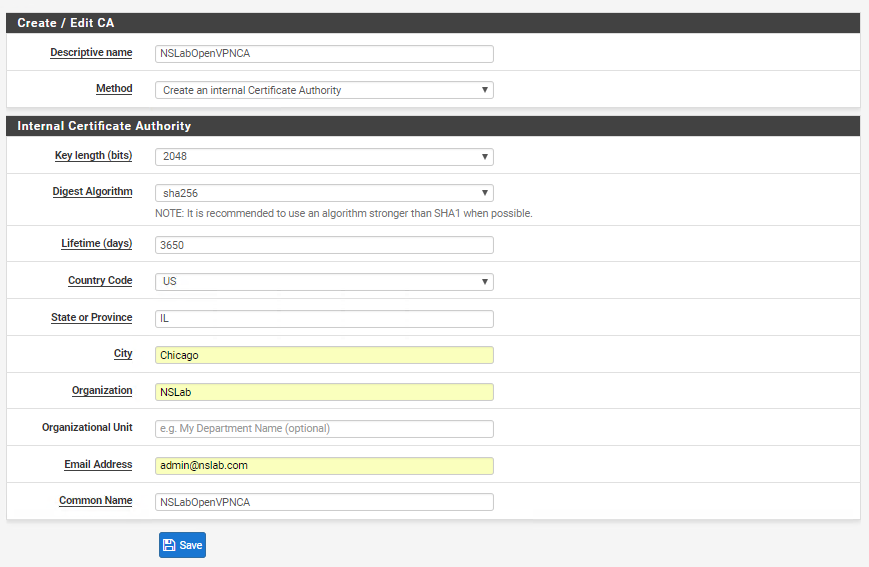
Let’s start by creating a Certification Authority (CA) that we will use to create certificates certificates. Log into the pfSense admin console and go to System > Certificate Manager > CAs and create a new CA with the following attributes (or similar):
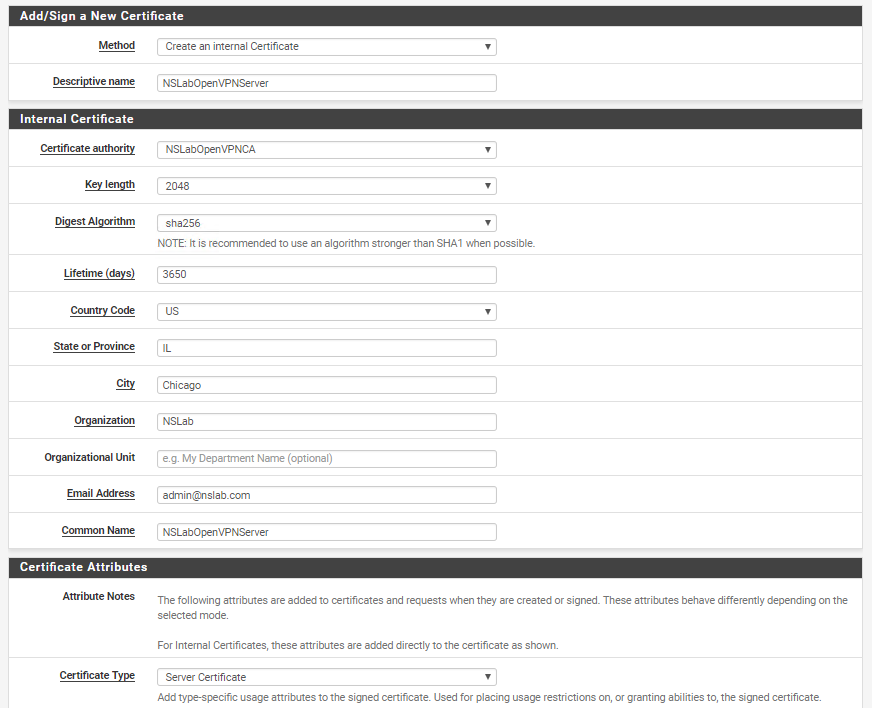
Then go to System > Certificate Manager > Certificates and create a new certificate for our OpenVPN server:
OpenVPN Server
pfSense comes already pre-installed with OpenVPN. Go to VPN > OpenVPN > Wizard and start creating a new Local User Access VPN server:
Choose NSLabOpenVPNCA as the CA and NSLabOpenVPNServer as the server certificate:
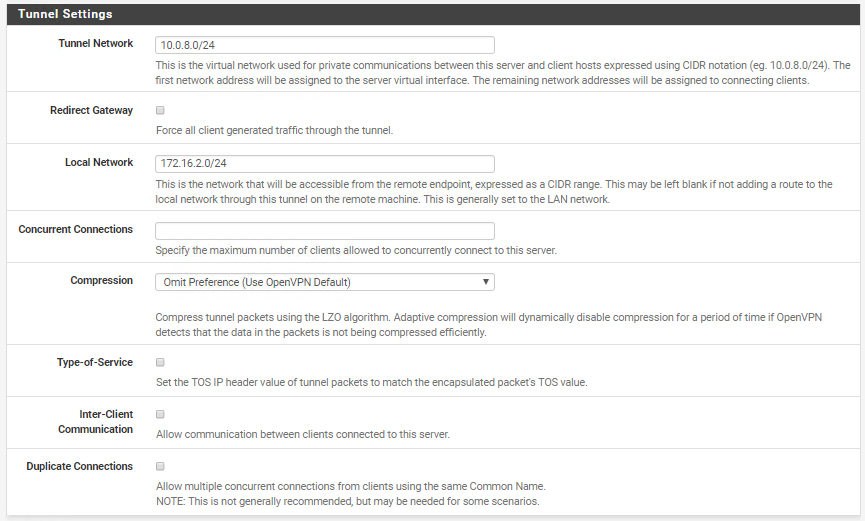
In the next page, use the default values for the Generic Settings and Cryptographic Settings but update the Tunnel Settings to make sure remote users connecting through the VPN can access the DMZ network (172.16.2.0/24):
Update the DNS and NTP client settings to point to the internal gateway (172.16.2.1):
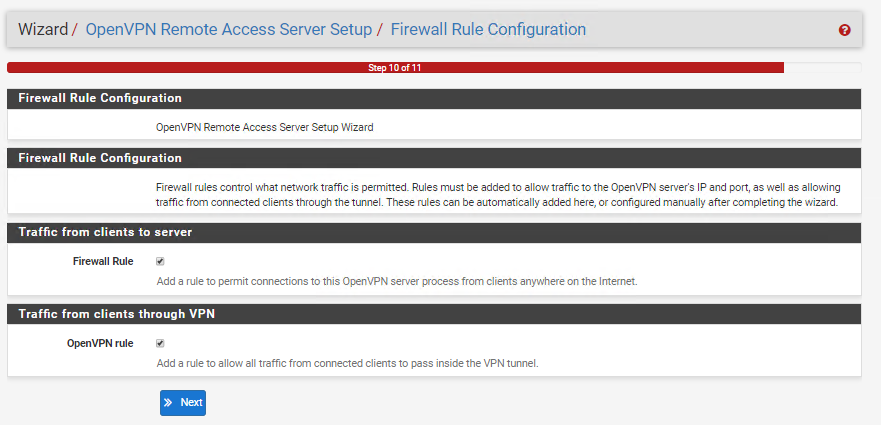
Finally, let the wizard create a new WAN rule to allow clients to connect to the OpenVPN port (1194) from the internet:
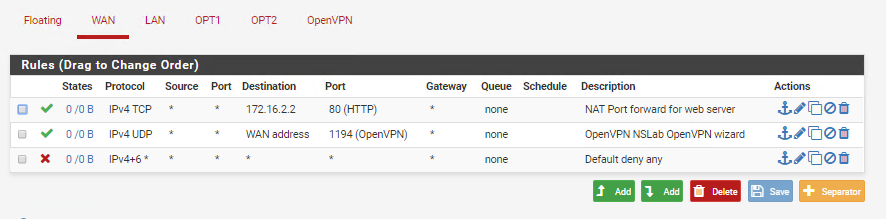
Your OpenVPN server is now configured. To verify the new firewall rules go to Firewall > Rules > WAN and make sure that the OpenVPN rule shows up above the “Default deny any” rule (*Move up the rule if it shows up at the bottom of the list):
A new interface called “OpenVPN” should’ve also been created:
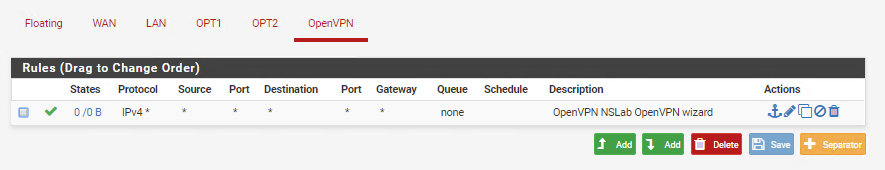
You can add rules to this OpenVPN interface if you want to filter the traffic entering the firewall across the VPN.
OpenVPN Client
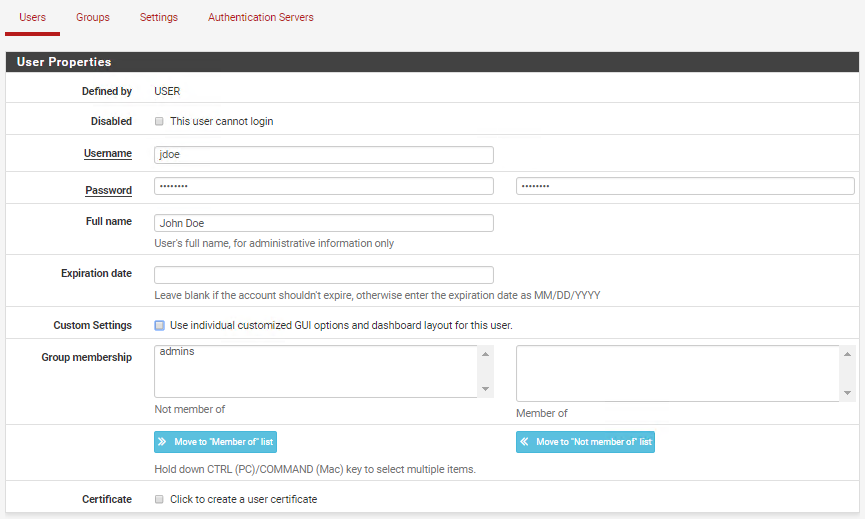
Now that our OpenVPN server is running and accessible from the internet we need to configure the OpenVPN client, but first, we need to create some test users. Go to System > User Manager > Users and create a new user:
Instead of creating the client configuration file from scratch we are going to install the OpenVPN Client Export package available for pfSense. Navigate to System > Package Manager > Available Packages, _search for “_openvpn-client-export”, and install the package:

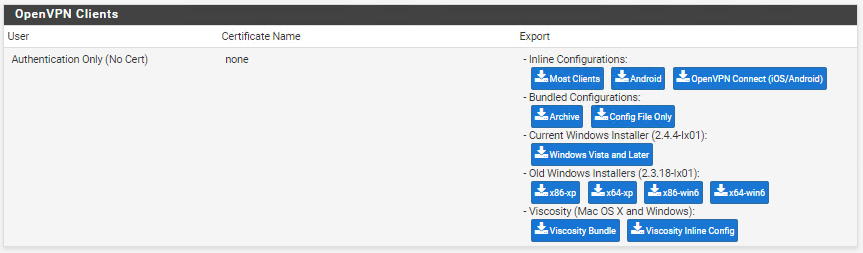
Then, go to VPN > OpenVPN > Client Export and click on “Inline Configurations - Most Clients”:
Transfer the .ovpn file to the nsClient VM and run the following command to install the OpenVPN client from the Ubuntu repositories:
$ sudo apt-get install openvpn
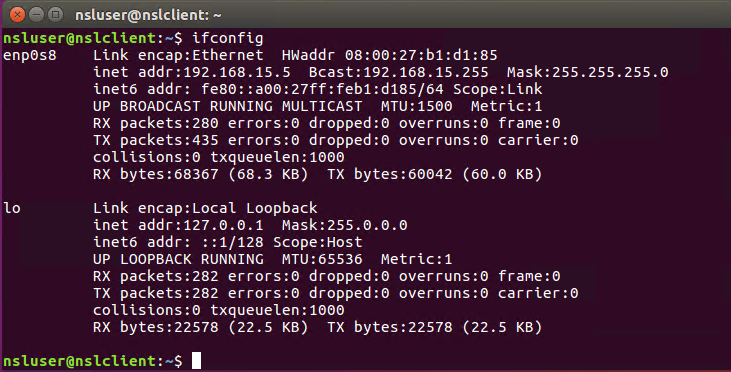
Verify that you are connected to the external network (192.168.15.0/24 in my case):
*Run the following commands to switch to the external network if you are connected to the internal network:
$ sudo ifdown enp0s3 $ sudo ifup enp0s8
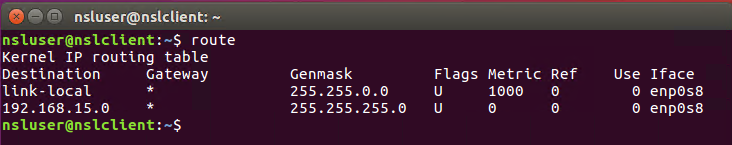
Verify also that there are only two IP routes in your internal routing table:
Next, open a different terminal and run the following command to connect to the OpenVPN server:
$ sudo openvpn --config \<path-to-ovpn-file\>
When prompted, provide the credentials of the test user you created earlier. If everything works fine you should see the following output:
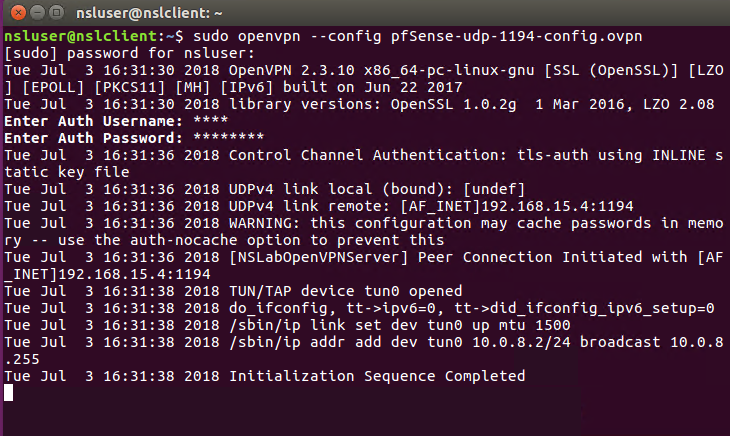
You should also see a new tun interface (all packets with destination 172.16.2.X will be routed through this interface):
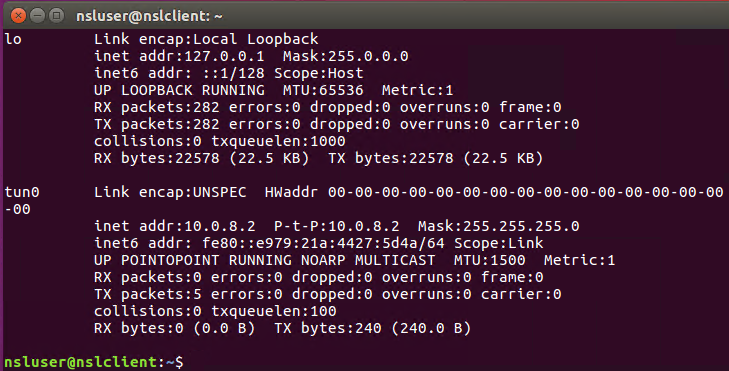
As well as a new IP route for the 172.16.2.0/24 network:
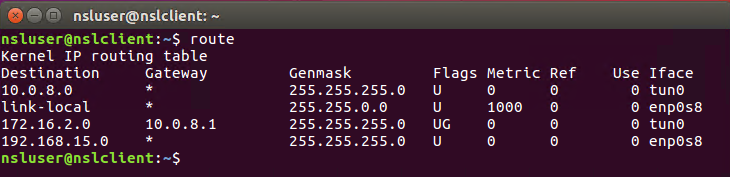
Finally, make sure you can connect to the web server using its internal IP address (172.16.2.2):
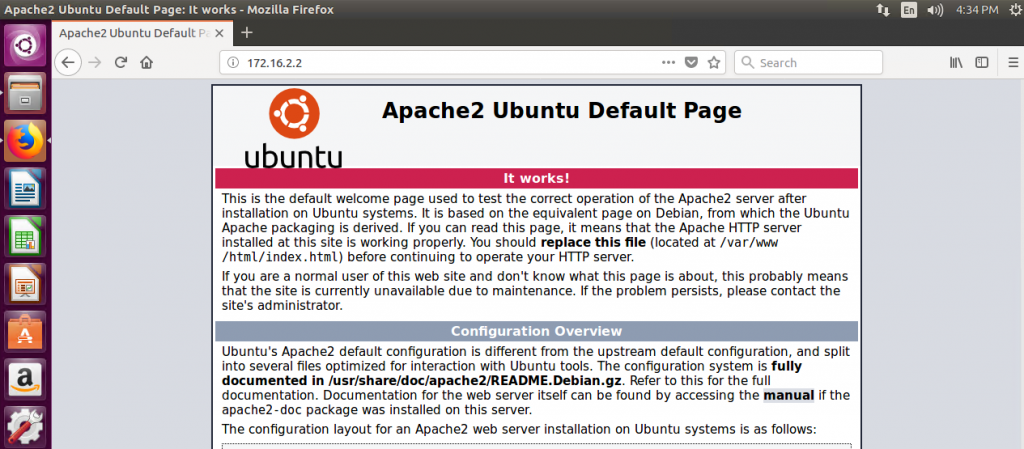
And that’s it for today!
I hope this post helped you understand how VPNs work a little better. Stay tuned for the next chapter on network security!